Oct 25, 2023
PTRZ-2023-1025
Carlos Garrido of Pentraze Cybersecurity
Throughout history, we have witnessed an incredible number of Windows functionalities being abused for malicious purposes, such as BitLocker being used in the development of Ransomware. This is one of the reasons why the author of this research has devoted time to understanding what other functionalities can be abused at the impact tactic level, which, in this case, will be Data Protection API (DPAPI).
LockBit ransomware — What You Need to Know
DPAPI has been the subject of multiple abuses aimed at extracting and accessing user and application secrets, as evidenced by techniques such as Credentials from Password Stores (T1555) and Credentials from Password Stores: Credentials from Web Browsers (T1555.003). While it may appear that an API like DPAPI is less likely to be abused when it comes to the Impact tactic, we will see that a malicious actor can develop a malicious artifact that abuses this function to encrypt a file system.
Credentials from Password Stores Credentials from Password Stores: Credentials from Web Browsers
All the research that will be shown below is, to a large extent, grounded in the principles of the Pyramid of Pain:
The Pyramid of Pain is a conceptual model for the effective use of Cyber Threat Intelligence in threat detection operations, with a particular emphasis on increasing the cost and/or difficulty of adversary operations to thwart them. For this reason, adversaries find themselves in the need or position to develop new procedures and techniques, in other words, they constantly need to reinvent themselves.
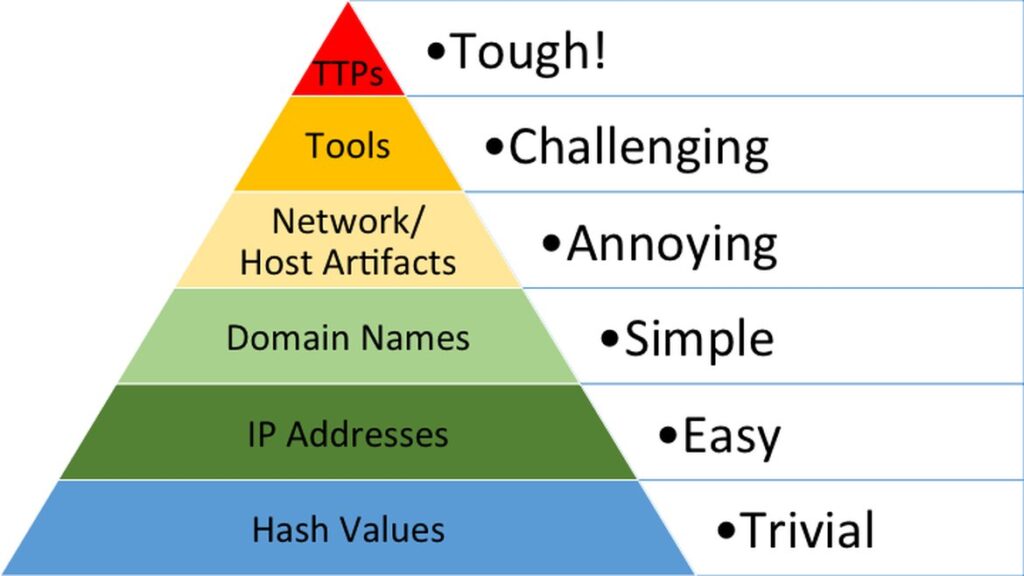
Image retrieved from AttackIQ - What is the Pyramid of Pain?
Since Windows 2000, Microsoft has equipped its operating systems with a new interface called the Data Protection Application Programming Interface (DPAPI) in order to protect all types of information. Within the operating system, we can observe the use of DPAPI in the Windows Credential Manager, Windows Vault, and the storage of wireless connection passwords.
DPAPI has become very popular among developers due to its simplicity, as it only requires calling the Win32 API functions CryptProtectData and CryptUnprotectData from the Crypt32.dll library to encrypt and decrypt, respectively.
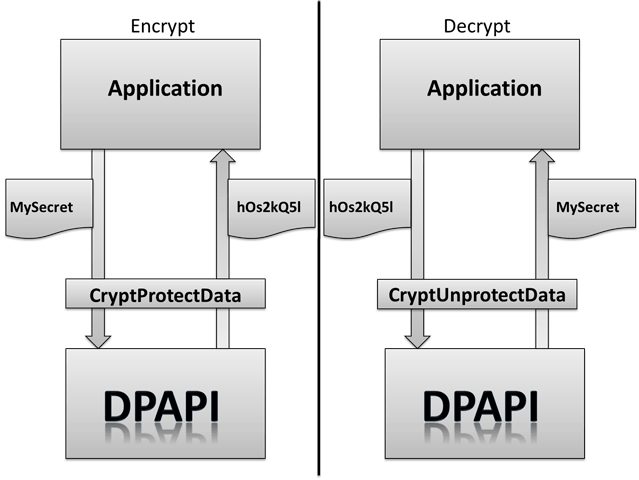
Image retrieved from passcape - DPAPI Secrets
According to official Microsoft documentation, we can use the CryptProtectData API to encrypt a DATA_BLOB type structure. Typically, only a user with the same logon credentials as the one who encrypted the data can decrypt it. Additionally, encryption and decryption are usually expected to occur on the same computer.
DPAPI_IMP BOOL CryptProtectData(
[in] DATA_BLOB *pDataIn,
[in, optional] LPCWSTR szDataDescr,
[in, optional] DATA_BLOB *pOptionalEntropy,
[in] PVOID pvReserved,
[in, optional] CRYPTPROTECT_PROMPTSTRUCT *pPromptStruct,
[in] DWORD dwFlags,
[out] DATA_BLOB *pDataOut
);
typedef struct _CRYPTOAPI_BLOB {
DWORD cbData;
BYTE *pbData;
} CRYPT_INTEGER_BLOB, *PCRYPT_INTEGER_BLOB, CRYPT_UINT_BLOB, *PCRYPT_UINT_BLOB, CRYPT_OBJID_BLOB, *PCRYPT_OBJID_BLOB, CERT_NAME_BLOB, CERT_RDN_VALUE_BLOB, *PCERT_NAME_BLOB, *PCERT_RDN_VALUE_BLOB, CERT_BLOB, *PCERT_BLOB, CRL_BLOB, *PCRL_BLOB, DATA_BLOB, *PDATA_BLOB, CRYPT_DATA_BLOB, *PCRYPT_DATA_BLOB, CRYPT_HASH_BLOB, *PCRYPT_HASH_BLOB, CRYPT_DIGEST_BLOB, *PCRYPT_DIGEST_BLOB, CRYPT_DER_BLOB, PCRYPT_DER_BLOB, CRYPT_ATTR_BLOB, *PCRYPT_ATTR_BLOB;
CryptProtectData function (dpapi.h)
Finally, it is very important to note that The function also adds a Message Authentication Code (MAC) (keyed integrity check) to the encrypted data to guard against data tampering.
The dwFlags parameter is of paramount importance as it allows us to enable very specific functions within DPAPI:
The most interesting flag is CRYPTPROTECT_AUDIT as it generates an audit on protect and unprotect operations:
It is of utmost importance to highlight that, according to Microsoft’s official documentation, the aforementioned events will only be generated if the CRYPTPROTECT_AUDIT flag is enabled.
From the adversary’s perspective, if these Win32 APIs were to be abused, they will obviously not activate that flag to “minimize” the chances of their operations being detected.
As previously explained, DPAPI typically uses the user’s logon credentials for encryption and decryption operation. However, the latter can change if the CRYPTPROTECT_LOCAL_MACHINE flag is specified, as it grants all local machine users the authority to decrypt (unprotect) the data. Consequently, if someone encrypts data with DPAPI (as in the case of ransomware), the victim is likely to recover their data without major issues, unless additional entropy is specified (pOptionalEntropy).
If the user or application provides additional entropy to encrypt the data, it must be used during the decryption phase without exception.
Next, we have a .NET developed proof of concept of the malicious artifact (DPAPI For Impact - Ransomware).
Essentially, the artifact will establish a connection via a secure channel (HTTPS) to a command and control server to download the additional entropy (pOptionalEntropy) into artifact’s memory, which, as we explained, will be the value that minimizes the chances of the victim recovering their information. Also, it is important to note that the malicious artifact takes the files and encrypts them in chunks without damaging the MAC (Message Authentication Code), this will prevent to corrupt the data being encrypted.
On the other hand, it is possible to enhance the sophistication of the malicious artifact by adding anti-forensic properties, for instance, deleting the key from memory immediately after it has been used for its purpose.
Note: This malicious artifact was tested multiple times on a Windows 11 machine and successfully managed to evade Windows Defender.
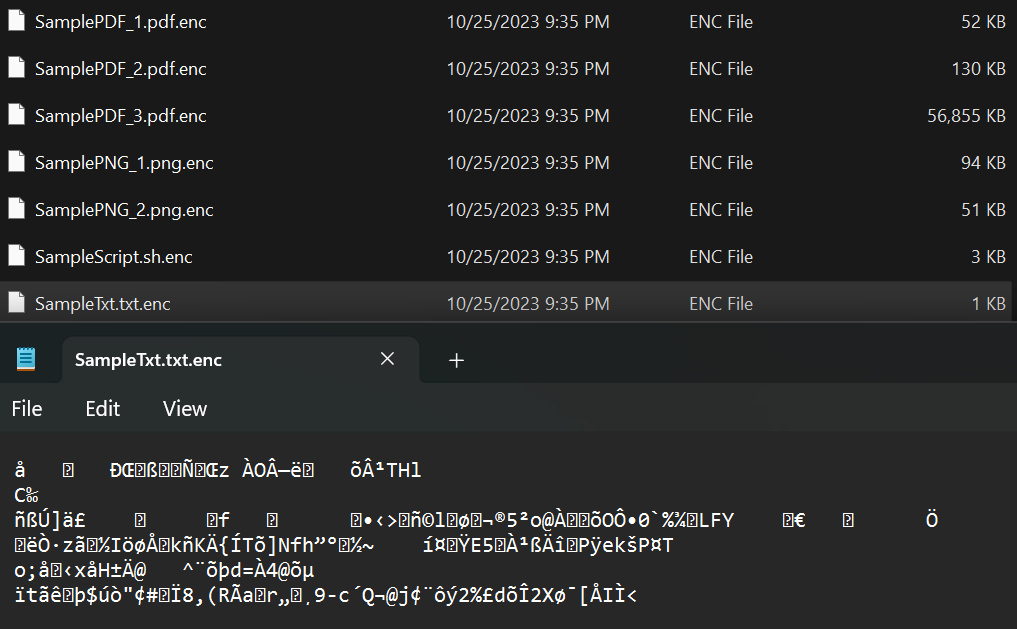
The only way to recover the data is by providing the right Optional Entropy when calling CryptUnprotectData.
A file exhibiting high entropy suggests that it is well-encrypted, well-compressed, or comprised of genuinely random data.
As an illustrative example, we will take one of the encrypted PDFs.
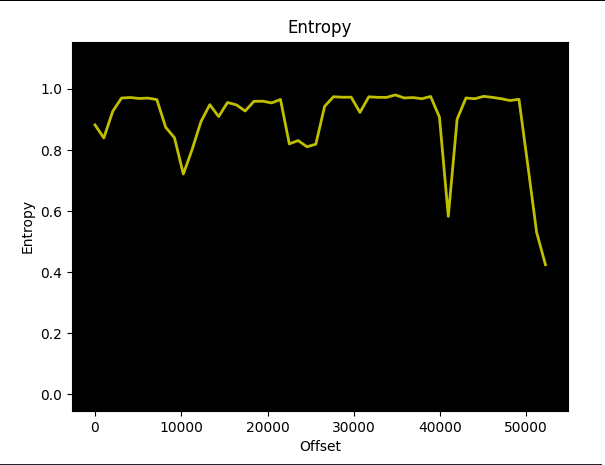
In the following graph, we observe the encrypted PDF entropy (0.980), approaching very close to the point of maximum entropy (1.0), and this value remains nearly constant across the file offsets:
EntropyCapture: Simple Extraction of DPAPI Optional Entropy by Matt Merrill

Evaluación proactiva utilizando tácticas, técnicas y procedimientos de atacantes reales para identificar fallas de seguridad, configuraciones incorrectas y vulnerabilidades.

Protección integral de aplicaciones, garantizando la seguridad en todas las fases del desarrollo.

Simulación avanzada de ataques cibernéticos para evaluar y mejorar la capacidad de respuesta de una organización.

Proceso proactivo para identificar, priorizar y abordar las vulnerabilidades de seguridad en sistemas y software, mejorando la defensa de una organización contra las amenazas cibernéticas en evolución.