Jul 11, 2023
CVE-2023-24491
Rilke Petrosky of Pentraze Cybersecurity
We’ve discovered a Loca Privilege Escalation vulnerability in the Citrix Secure Access client for Windows allowing an unprivileged local users to execute programs in the context of the NT AUTHORITY\System user.
The following supported versions are affected by the vulnerability:
7.8 (High) - CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H
The Citrix Secure Access elevated service process (nsverctl.exe) provides an In-proc RPC server through a COM interface that can be abused from the Citrix NS client (nsload.exe) to call privilege operations such as arbitrary Windows registry read and write access, and service update and uninstallation.
Before allowing calls to the COM interface, the client application must authenticate by sending a key over the service process’ named pipe (\\pipe\CitrixNgServer), triggering a code signature validation with Windows WinVerifyTrust function.
We’ve found some ways to bypass the file integrity and WinVerifyTrust code signature check, as this function only verifies the file on disk and disregards memory modifications.
Our exploit patches the client application and injects a DLL in order to alter the execution flow, abuse the CnsServer::ns_serverregapi function to modify the uninstall command (SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\(product-key)\UninstallString), and then call the uninstall procedure (CnsServer::ns_LaunchUninstaller) which runs in the context of the NT AUTHORITY\SYSTEM user.
Even thought the server authenticates the client executable through code signing and unique hash shared through named pipes, and regardless of it’s recent CFI and CFG mitigations, it is still possible to inject code into the running process and thus hijack the service and network driver control.
Exploit Chain:
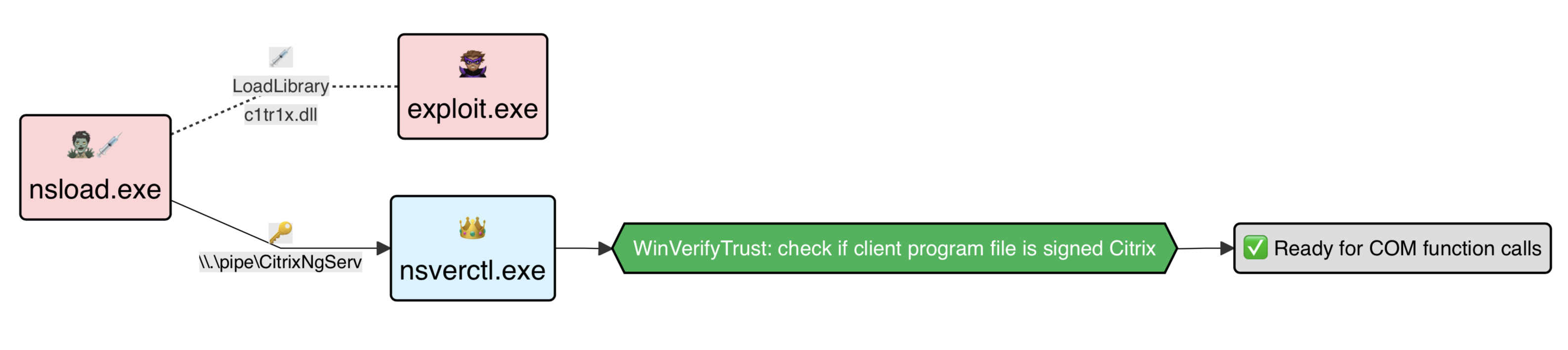
Inject exploit DLL into client application (NSload.exe).
Abuse the CnsServer::ns_serverregapi registry writing functions to replace the uninstall program string with the exploit code found on SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\(product-key)\UninstallString
Force the client’s execution flow to call the CnsServer::ns_LaunchUninstaller function, triggering an elevated execution of the exploit program.

Proactive assessment using tactics, techniques, and procedures of actual attackers to identify security flaws, incorrect configurations, and vulnerabilities.

Comprehensive application protection, ensuring robust security throughout the entire software development lifecycle.

Simulate and emulate advanced cyber attacks to pinpoint vulnerabilities and test your organization's defense mechanisms, ensuring robust resilience against real-world threats.

Proactive process to identify, prioritize, and address security vulnerabilities in systems and software, enhancing an organization's defense against evolving cyber threats.